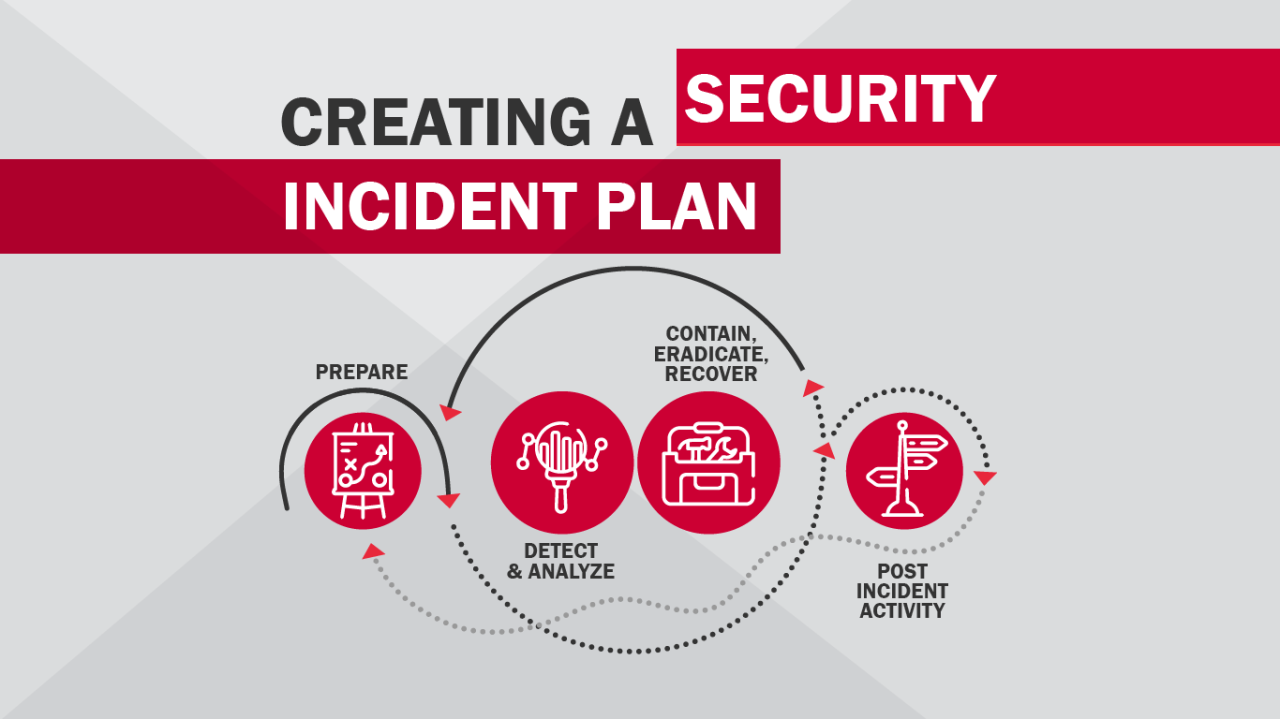
Cybersecurity incidents happen more often than people expect. Even well-protected systems can face attacks, mistakes, or failures. Because of this, organizations must be prepared to respond quickly and safely when something goes wrong.
A Cybersecurity Incident Response Plan provides a clear path to follow during a security event. Instead of panic and confusion, teams know what to do, who is responsible, and how to limit damage.
This article explains the key steps in a cybersecurity incident response plan. It focuses on real-world practices, clear processes, and how structured response helps reduce risk, protect data, and restore normal operations.
Read also: Is Cyber Security a Good Career?
Understanding Cybersecurity Incident Response
What is a cybersecurity incident?
A cybersecurity incident is any event that threatens the confidentiality, integrity, or availability of digital systems or data. This may include malware infections, phishing attacks, data breaches, or unauthorized access.
Not every alert is a crisis. However, every alert must be reviewed carefully to determine risk.
Why incident response planning matters
Without a plan, teams react slowly and make mistakes. A structured Incident Response approach helps reduce downtime, prevent data loss, and limit long-term damage.
Planning also supports compliance, accountability, and trust.
Step 1: Preparation
Building readiness before an incident occurs
Preparation is the most important step in any Cybersecurity Incident Response Plan. Teams must be ready before an incident happens.
This includes defining roles, creating response procedures, and training staff. Preparation reduces confusion when time is critical.
Creating policies and communication plans
Clear policies explain how incidents are reported and escalated. Communication plans ensure the right people are informed quickly.
Preparation also includes backups, access controls, and security awareness training.
Step 2: Identification
Detecting potential security incidents
Identification is the process of recognizing that an incident may be happening. Alerts may come from monitoring systems, user reports, or unusual activity.
At this stage, teams collect evidence without rushing to conclusions.
Distinguishing real incidents from false alarms
Not every alert is a real threat. Teams must analyze logs, system behavior, and data patterns to confirm whether an incident exists.
Accurate identification prevents wasted effort and unnecessary disruption.
Step 3: Containment
Limiting damage and stopping spread
Once an incident is confirmed, containment begins. The goal is to stop the threat from spreading further.
You can prevent the damage by isolating the affected systems, disabling all the affected accounts, or blocking malicious traffic.
Short-term and long-term containment strategies
Short-term containment focuses on immediate control. Long-term containment ensures systems remain stable while recovery planning continues.
Both approaches work together to protect the environment.
Step 4: Eradication
Removing the root cause of the incident
Eradication involves removing malware, closing vulnerabilities, and eliminating unauthorized access.
Teams must identify how the incident started to prevent repeat attacks.
Fixing weaknesses in systems and processes
This step often reveals gaps in security controls. Fixing these weaknesses strengthens overall Cybersecurity posture.
Eradication prepares systems for safe recovery.
Step 5: Recovery
Restoring systems and services safely
Recovery focuses on bringing systems back online in a controlled way. Backups are restored, systems are tested, and services resume gradually.
Rushing recovery can cause reinfection or data loss.
Monitoring for recurring issues
After restoration, systems are closely monitored. This ensures the threat is fully resolved and no hidden issues remain.
Recovery is successful only when stability returns.
Step 6: Lessons Learned
Reviewing what happened and why
After the incident, teams review the event in detail. They analyze timelines, decisions, and outcomes.
This step turns incidents into learning opportunities.
Improving future incident response plans
Lessons learned lead to updated procedures, better tools, and stronger defenses.
Continuous improvement in your system is the main and most important principle of effective Incident Response.
Roles and Responsibilities in Incident Response
Importance of clear ownership
Every response plan defines who does what. Clear ownership prevents confusion and delays.
Technical teams, management, and communication roles must work together.
Coordination across teams
Incident response often involves IT, security, legal, and leadership teams. Coordination ensures consistent decisions and messaging.
Good teamwork reduces impact.
Communication During a Cybersecurity Incident
Internal communication best practices
Teams must share accurate information quickly. Clear updates help align actions and reduce panic.
Confusing communication increases risk.
External communication considerations
In some cases, external communication is required. Transparency and accuracy are critical.
Well-planned communication protects trust and credibility.
Importance of Documentation
Recording actions and decisions
Documentation captures what happened, what was done, and why. This supports accountability and learning.
Accurate records also help with audits and compliance.
Supporting future improvements
Documentation helps refine response plans. It ensures improvements are based on real experience.
Incident Response and Risk Management
Reducing long-term cybersecurity risk
Incident response is part of broader Risk Management. Each incident reveals areas for improvement.
Strong response plans reduce future risk exposure.
Aligning response with security strategy
Incident response supports overall cybersecurity goals. It connects prevention, detection, and recovery into one system.
Alignment improves resilience.
Common Challenges in Incident Response
Delayed detection and response
Late detection increases damage. Strong monitoring and training reduce delays.
Prepared teams respond faster and safer.
Lack of coordination or training
Untrained teams struggle under pressure. Regular exercises improve confidence and performance.
Practice makes response plans effective.
Incident Response Testing and Simulation
Why testing an incident response plan matters
An incident response plan is only useful if it works in real situations. Therefore, regular testing is essential. Testing helps teams find gaps, unclear steps, or missing roles before a real incident occurs.
Without testing, teams may freeze or make mistakes during an actual Cybersecurity Incident.
Common types of incident response exercises
Organizations often use tabletop exercises, simulated attacks, or walkthroughs. These activities allow teams to practice decision making in a safe environment.
As a result, response time improves and confidence increases.
Role of Automation in Incident Response
How automation supports faster response
Automation helps speed up detection and response. Automated alerts, system isolation, and log analysis reduce manual effort.
However, automation works best when assisted by a human.
Balancing automation with human control
Automated systems can act quickly, but humans must review decisions. This balance prevents errors and supports Responsible Cybersecurity practices.
Incident Response and Business Continuity
Connection between incident response and continuity planning
Incident response is closely linked to Business Continuity. While response focuses on stopping the threat, continuity focuses on keeping operations running.
Together, they reduce downtime and financial loss.
Protecting critical systems and services
Organizations must identify critical systems in advance. During an incident, these systems receive priority protection and recovery.
Planning ahead reduces chaos during emergencies.
Legal and Compliance Considerations
Why compliance matters during incidents
Some incidents require legal reporting or documentation. Following regulations protects organizations from penalties and legal risk.
Clear procedures ensure compliance is handled correctly.
Importance of evidence preservation
During an incident, evidence must be preserved carefully. Logs, files, and timelines may be needed for investigation or audits.
Good documentation supports transparency and accountability.
Cybersecurity Incident Response Metrics
Measuring response effectiveness
Metrics help teams understand how well they responded. Common measures include detection time, containment time, and recovery time.
Tracking these metrics helps improve future responses.
Using metrics to improve security posture
Metrics reveal weaknesses in detection or communication. Over time, teams use this data to strengthen defenses and reduce risk.
Incident Response for Different Threat Types
Responding to phishing and social engineering attacks
Phishing incidents often involve compromised accounts. Response focuses on account security, user awareness, and email controls.
Education plays a key role in prevention.
Handling malware and ransomware incidents
Malware incidents require system isolation, cleanup, and recovery from backups. Ransomware response prioritizes containment and data protection.
Preparation reduces damage significantly.
Importance of Continuous Improvement
Updating the incident response plan regularly
Cyber threats change over time. Therefore, incident response plans must be reviewed and updated regularly.
Outdated plans reduce effectiveness.
Learning from industry incidents
Studying public cybersecurity incidents helps teams understand common attack patterns and response mistakes.
Learning from others strengthens readiness.
Human Factor in Incident Response
Stress management during incidents
Incidents create pressure. Clear roles and rehearsed plans reduce stress and improve decision quality.
Calm teams respond better.
Importance of leadership during response
Strong leadership provides direction and clarity. Leaders support teams, prioritize actions, and ensure consistent communication.
Good leadership improves outcomes.
Conclusion
A well-structured cybersecurity incident response plan helps organizations respond calmly and effectively when security incidents occur. Instead of guessing, teams follow clear steps that limit damage, protect data, and restore systems.
By focusing on preparation, identification, containment, eradication, recovery, and lessons learned, organizations build stronger defenses over time. Cybersecurity, Incident Response, and Risk Management work together to support long-term resilience.
Cyber threats will continue to evolve. However, a strong incident response plan ensures that when incidents happen, teams are ready to act with clarity, control, and confidence.
Read also: Navigating the Future: Remote Digital Marketing jobs Success